Hello Everyone
It’s Andrew with the latest edition of the NetScaler Times, an update to keep you up-to-date on all things NetScaler-related! Why read this? To make you soar with the eagles 🦅 !
The idea is to pull together events, firmware releases, support articles, and anything else I think is relevant into a single email.
High-level agenda for this week:
The newsletter provides updates on firmware builds, including that there are no new builds this week, and clarifications on some End of Life (EOL) dates.
The newsletter highlights NetScaler security updates, including a security bulletin update for CVE-2024-5491 and CVE-2024-5492, last modified on 12/Mar/2025, and a NetScaler WAF Signatures Update v152 updated on 12th May.
The newsletter also provides links to various NetScaler-related web updates, Citrix Cloud Native Networking hands-on guides, and requests feedback which can be sent to Andrew.Scott@cloud.com.
1. The latest firmware builds.
Below are the details for the various builds, which can help you plan for new releases in your environment. This support document has more information on the different release cycles.
NetScaler has multiple form factors to support different environments. It is built on a single operating system with a software-based architecture, so its behavior will be the same regardless of whether it is used as hardware, a virtual machine, bare metal, or a container. Pick one that works for your environment and needs.
Latest Build Versions:
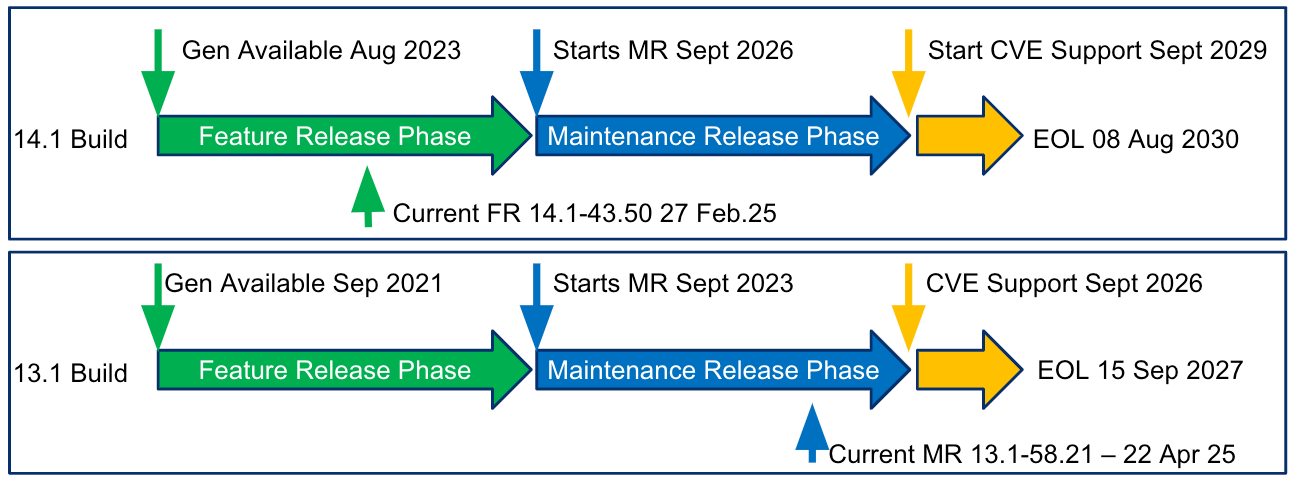
Here is a timeline for the 14.1 and 13.1 builds to show where they are within their respective release lifecycle.
Here are all the firmware builds in a table:
Notes about Builds:
There are no new builds this week.
I have clarified a few build EOL dates in the above table.
The above is a summary taken from the NetScaler Section here.
For 13.1 FIPS & NDcPP builds: On the downloads page, there are two places to get the 13.1 NDcPP build. The FIPS build is dual-certified now and is slightly newer than the NDcPP-only build. One to watch if you use those builds.
FIPS FAQ - NetScaler FIPS FAQ - Link
Which release should I use?
The release families are designed such that 14.1 has more elements changing with each update, hence the feature phase designation. There will be fewer changes in 13.1.
An example of the move to 14.1 might be that you want to take advantage of removing the dependency of ALB in Azure with your NetScaler HA deployment. Read more here. This could save some $$$ (insert local currency).
Also, a recent customer request included plans to build a new Azure infrastructure. This was not expected to be a short-term deployment. Looking at the build cycles above, it would make sense to start looking at 14.1 for this. This would avoid having to re-architect the solution next year when 13.1 moves to CVE-only support.
What about NetScaler SDX?
There are multiple NetScaler designations. VPX, MPX, SDX, BLX, and CPX all use the same firmware. The table above applies to all NetScaler types. It might not be the same download file, as appliances like the SDX do have other elements to update.
End Of Sale Appliances & End of Life Appliances
There are some short lists below with the more recent appliance changes.
EoS Appliances
These appliances are End of Sale (unavailable to buy new now), they will live and run for 5 more years from 2024.
EOL Appliances
A table shows the significant EOL appliance events for the next 12 months. Last month (April), a few appliances reached their end of life and must be replaced. The MPX/SDX 16000 is the replacement.
2. Latest NetScaler Security updates
NetScaler ADC and NetScaler Gateway Security Bulletin for CVE-2024-5491 and CVE-2024-5492.
CTX Number: CTX677944
Article Type: Security Bulletin
Created Date: 9/Jul/2024
Last Modified Date: 12/Mar/2025
Severity: High
This was a security article released last year, it was updated on 12th March. More here
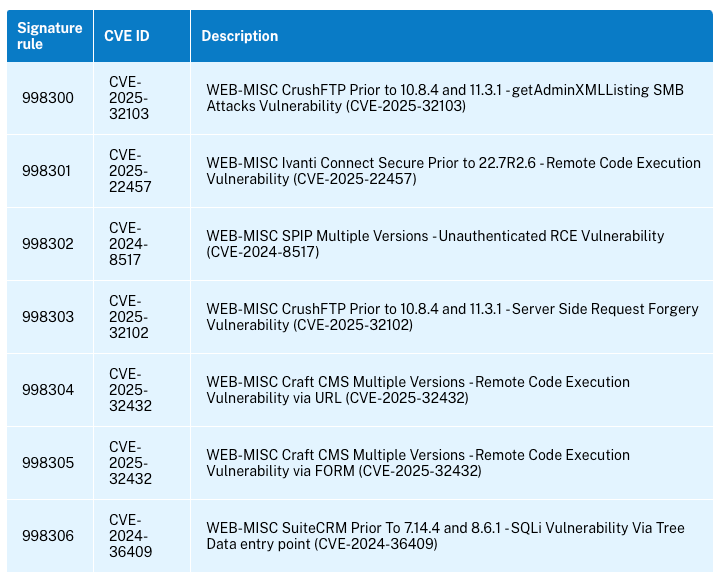
NetScaler WAF Signatures Update v152 was updated on the 12th May.
New signature rules are generated for the vulnerabilities identified in the week 2025-05-07. You can download and configure these signature rules to protect your appliance from security vulnerable attacks.
Link to details.
3. NetScaler-related web updates from…
Citrix NetScaler Automated backup job is failing after ...
3 days ago — After upgrading to NetScaler firmware 13.1.56.x or later, attempts to download backup files using the Nitro API may fail. Customers using automation tools ...
Duo Single Sign-On for NetScaler
4 days ago — Duo Single Sign-On is our cloud-hosted SSO product, which layers Duo's strong authentication and flexible policy engine on top of NetScaler logins.
Configure the built-in agent to manage instances
4 days ago — NetScaler Console supports management and monitoring of NetScaler instances using built-in agents. However, the following features are not supported in the ...
Provisioning NetScaler VPX instances on Microsoft Azure
4 days ago — NetScaler Console allows you to automate the deployment, setup, and management of the NetScaler VPX instances on Azure.
Documentation - Ansible Galaxy - netscaler.adc
6 days ago — The collection provides Ansible modules to configure and manage NetScaler ADC appliances. The modules are written using the NITRO API.
4. Citrix Cloud Native Networking (CNN) hands-on guides
My colleague Komal Bhardwaj pointed me to this resource, if you need to get your head around CNN, it is a great place to start!
Citrix cloud-native solutions leverage the advanced traffic management, observability, and comprehensive security features of Citrix ADCs to ensure enterprise-grade reliability and security. Let’s get started with CNN GitHub!
You’ll learn how to:
Deploy Citrix Ingress Controller for Citrix Cloud Native stack
Deploy Citrix ADC containerized proxy - CPX
Deploy Citrix Cloud native stack in different K8s platforms (On-prem, OpenShift, Rancher, EKS, AKS, GKE, PKS)
Deploy the Citrix Cloud native stack for
Unified Ingress topology
Two-tier topology
Service Mesh Lite topology
ISTIO: Service Mesh topology
More here
5. Feedback for this newsletter
Naturally, if something you feel should be added/removed or called out, drop me a note at Andrew.Scott@cloud.com. All mistakes are mine 🤭. All opinions expressed in this newsletter are solely my own and do not express the views or opinions of my employer. ☺️
You can get all the previous newsletters plus other articles here:
Have a great week!