30 days of ADM: Day 3 September 30, 2022
security analytics
I am back, it’s day 3!
Do you have a fox in the hen house? Some of the more recent security breaches have been sourced from internal threats, with this in mind maybe you need to take another look at how open are your internal resources are to access? When I say internal resources, I am actually being quite specific by saying Web applications. Naturally, anything external facing is going to get looked at too.
You have been selected for a training course in Citrix ADM, the goal is to provide you with enough information to be actually dangerous when talking to a customer or client. 30 days is a bit of an arbitrary number, but I am prepared to give you 2 minutes of material, can I get 2 minutes of your time? I have already talked about fleet management & more general analytics.
Day 3 will be specifically on Security analytics.
What are Security Analytics?
The purpose of Security Analytics is to tell you what kind of security threats your applications are being exposed to, it also provides some assessment of the way in which the appliance has been configured. Together, when you are armed with this information, you can better understand what is actually going on.
So what? What problem does it solve?
In one word, it gives you insight. Insight to better estimate your current risk. Understanding risk allows you to then make some decisions about how the service should be set up and run. This might mean that access to the application might only be necessary for people based in a certain area or location. I mean, if you live in London, a map of fish and chip shops in another part of the country might not be applicable.
Who needs to know this?
Anyone who runs a NetScaler for a service that is public-facing, as it allows them to be better informed.
What is the benefit of using ADM for this?
ADM provides a graphical user view that is simple to see and understand. Of course, there are other providers that offer this. The idea of this piece was to show that some really useful views will make the site owner’s job easier.
Ok, so what does it look like?
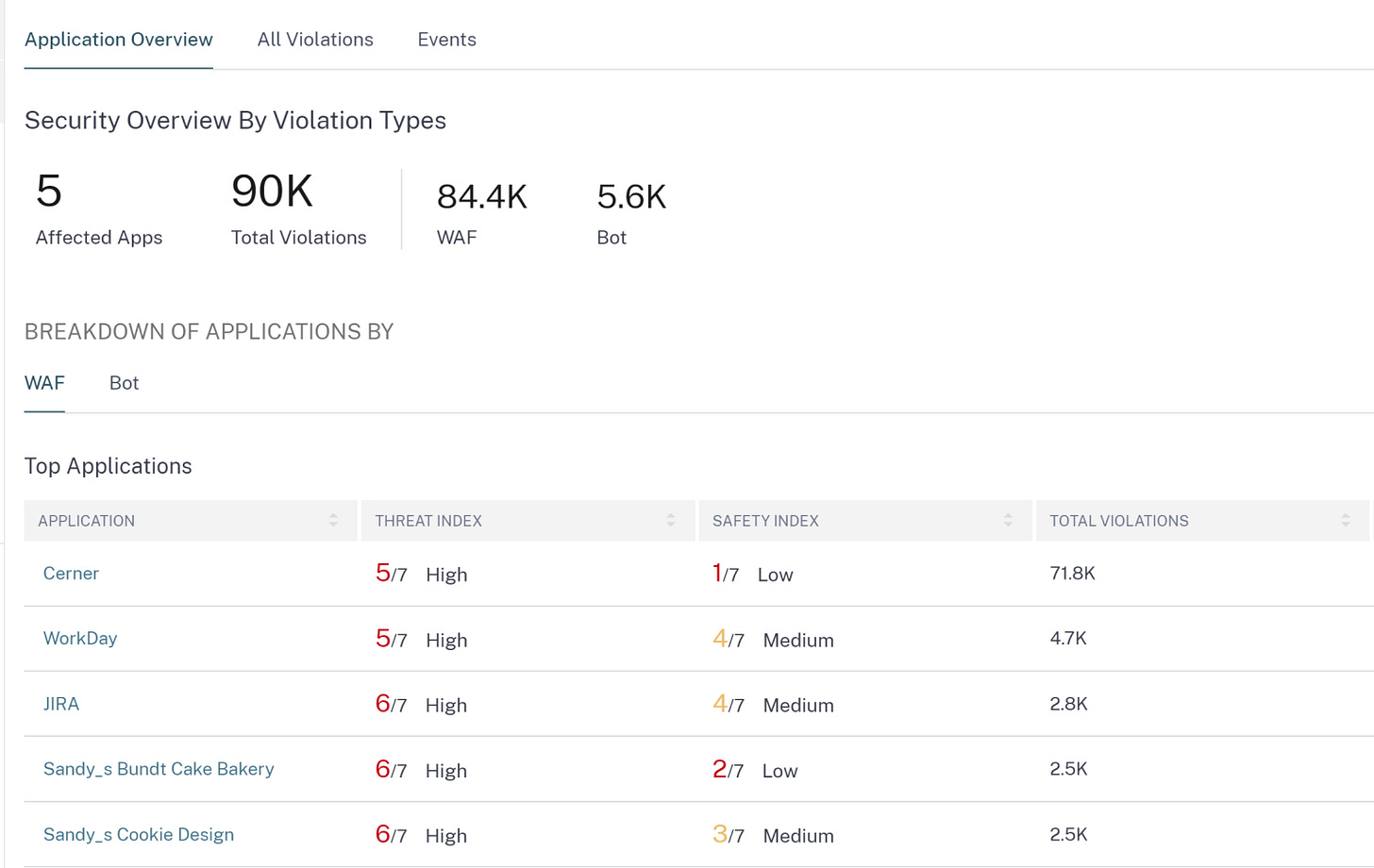
The Threat index shows how bad actors are trying to break in, it will show the specific attack. The safety index is how bad did it get set up in the first place? There is a line for each published application, as they all have their own scores based on their risk.
Looks like just a WAF then?
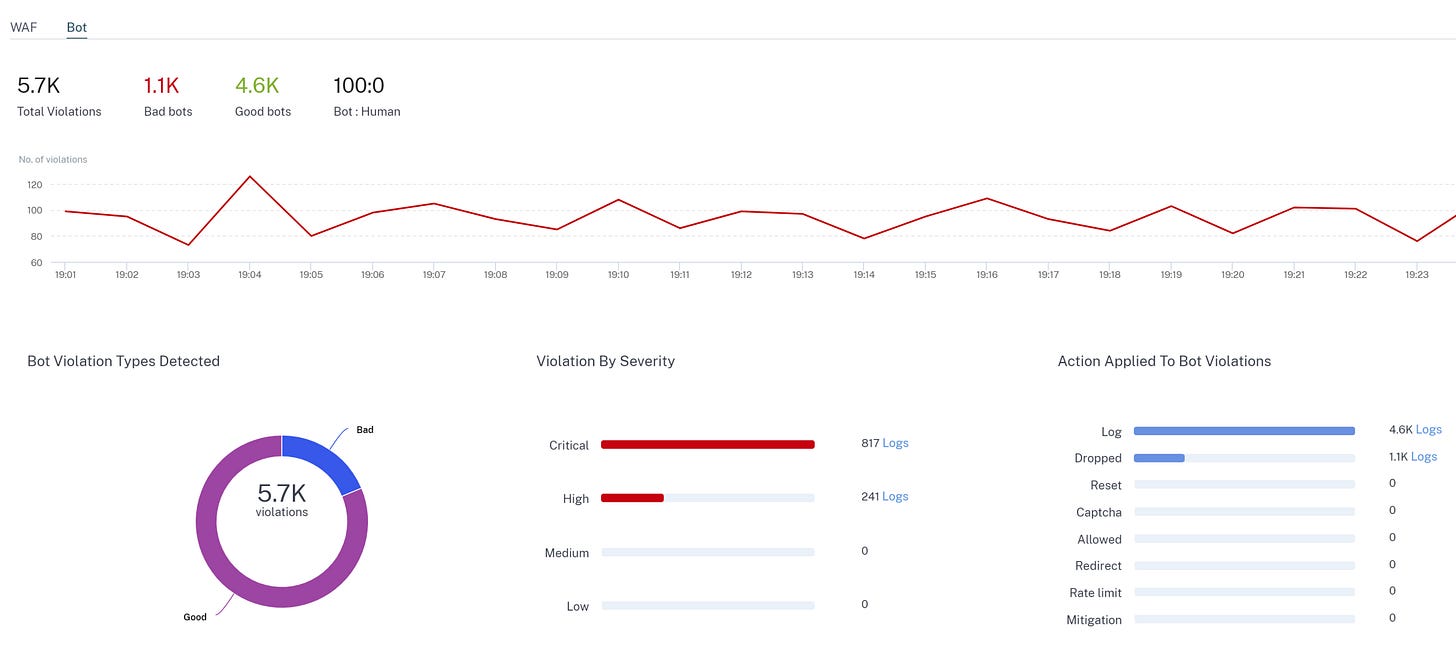
It also has the option to filter out BOT traffic. Large amounts of internet traffic is BOT based, they break down into good and bad types. Obviously, bad BOT's are unwanted.
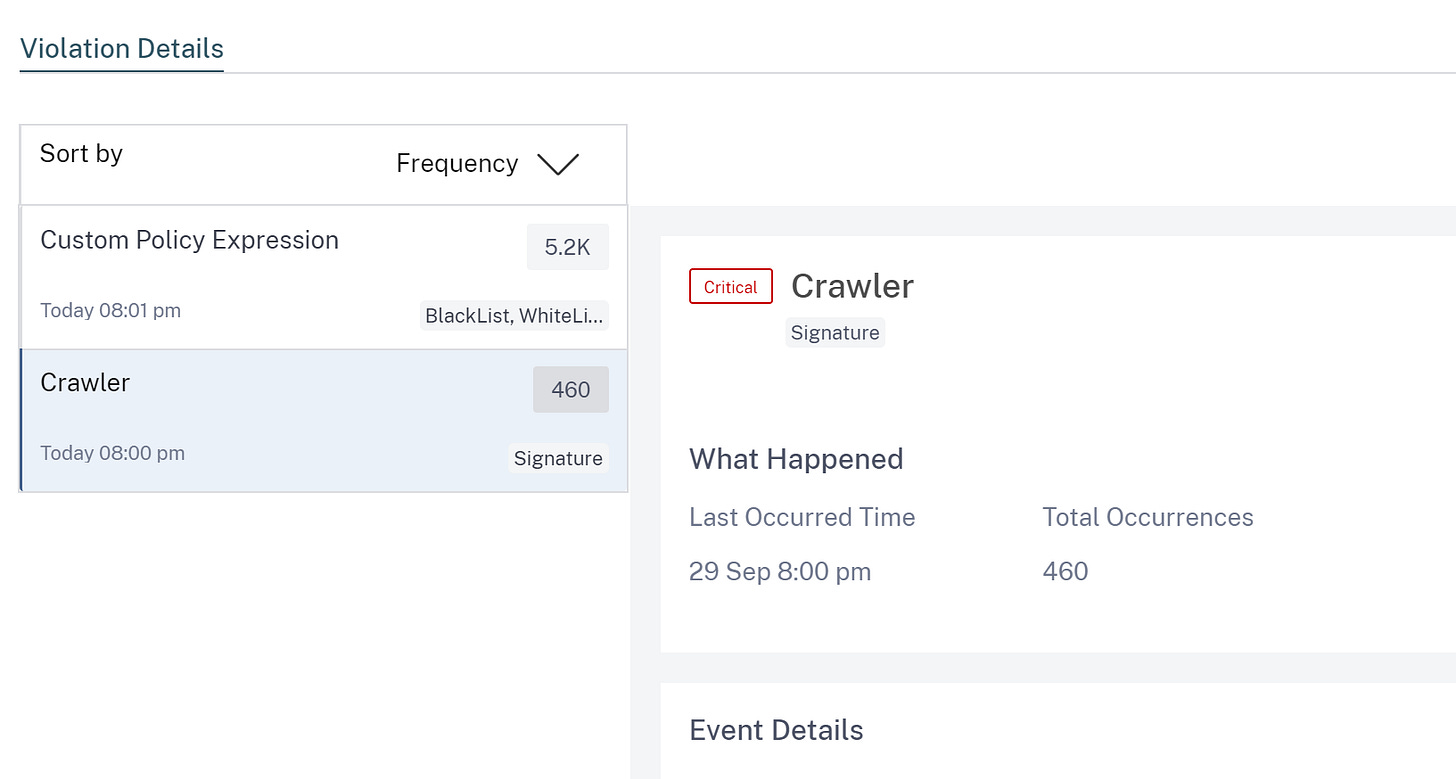
Here is some details on a specific BOT
I picked out a Crawler warning, as they can be used to tie up resources, but then offer nothing in return. While you service all the crawlers, legitimate user get a poor user experience and go elsewhere. Yikes!
Summary.
Security Analytics is a powerful option that ADM offers, just getting sight of what the bad guys are trying to do does allow you to take action, that could be a specific attack or something more generic like BOT loading. BOTs can consume resources and offer no business value, so they are something to know about and deal with. When using NetScaler with ADM, you can do that.
BTW, this capability is free for the first 2 Virtual servers! You can add packs of VIPS to cover off more than that.
What’s not to like?