30 Days of ADM: Day 8 October 08, 2022
Security advisory
I am back, it’s day 8!
The boss lady from yesterday walks into your office. She says that she has an email saying there is a CVE out for some specific NetScaler builds. You say you have it covered as upgrade advisory can tell you which builds are deployed where. You read the blog from yesterday…..
She, then asks. Which builds are affected? Where are we exposed?
YIKES!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
If only there was another part to upgrade advisory? There is!!!
You have been selected for a training course in Citrix ADM, the goal is to provide you with enough information to be actually dangerous when talking to a customer or client. 30 days is a bit of an arbitrary number, but I am prepared to give you 2minutes of material, can I get 2 minutes of your time? I have talked about Fleet management, general analytics, security analytics, AI / ML, Stylebooks, Pooled Capacity, and instance advisory upgrade
Today is all about the security advisory.
Honestly, what are you talking about?
The NetScaler appliance runs a software release that gets updated from time to time. This software version does need to be updated occasionally. This can be due to a software bug in one of the features that you are using, or it could be a new feature that has been added.
There are also security updates added to the software. The update process is necessary to keep you up to date.
So what? What problem does it solve?
It gives you a single view of what you have deployed where, it also shows very clearly how many appliances you have on what release. It also shows exactly, what appliances are affected by what security issues and then says how to get them updated.
Who would be interested in this?
Anyone who runs a NetScaler for something internet-facing, as it allows them to be more informed about risk for their workloads.
Where does ADM fit in?
ADM will offer the GUI to see the status of your appliances across the whole estate.
What does it look like?
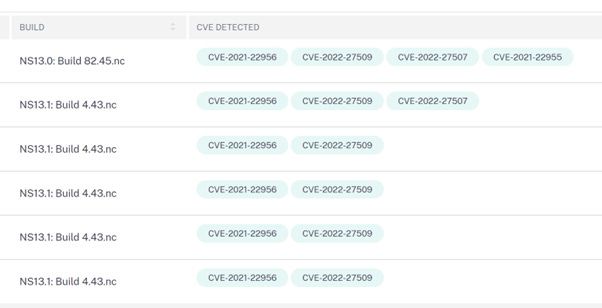
Getting a view of what you have, and which firmware release you have on what box is simple. It looks like this:
Call outs from the picture above:
1. The CVE is listed with the severity, so you can assess the risk directly.
2. The date of the CVE and a summary of what the CVE is about.
3. It does a scan to check your estate, but you can get it to have another look at things if they have changed since the last scan.
4. You can see how many appliances are affected by which CVE’s.
The combination is a killer capability.
Ok, what else?
There is then a link to sort out the instances that might need a bit of TLC
I have shown the builds with the corresponding CVE’s but this was taken from an appliance list.
Any more to this?
You can then get ADM to help fix all the issues. You just choose the workflow that suits.
Summary.
For me, this is an essential use case!
Ultimately, it’s another killer feature that is enabled with ADM service.
It’s free too, with the ADM service.
What’s not to like?